Email security in Office 365
There are various ways of security in office 365, this time I walk you thru the security possibilities for Email. As we start with the basics, we have the option to use an SPF record to protect us from spam on a very basic level. This is so basic and a requirement when you add the domain to Office 365.
As we go deeper into the security of the mail flow we see DKIM and DMARC. These two are not often used, but useful and easy to set up. So easy that it should be a requirement like SPF in my opinion.
Setup DMARC
Setting up DMARC is very easy and requires one DNS record on your domain. For using it with Office 365, your primary MX record should point to the EOP endpoint. The DNS records value is “_dmarc” and the value should be similar to this “v=DMARC1; p=quarantine; rua=mailto:; ruf=mailto:; pct=25; sp=none; fo=1;” You can generate the value on several websites like https://www.dmarcanalyzer.com/dmarc/dmarc-record-check/
The policy that can be set to “Monitor”, “quarantine” or “reject”. For Office 365 there is no difference in behavior for “quarantine” and “reject”. It is recommended to use a tool to monitor your mail flow and start with the policy “monitor”. This will allow you to see what mail fails the DMARC, so you can correct this.
Setup DKIM
The setup for DKIM is very similar to DMARC and requires two DNS records and one setting in Office 365. You need SPF and DMARC setup before enabling DKIM.
The DNS records are: Name: selector1._domainkey Type: CNAME Value: selector1-._domainkey..onmicrosoft.com.
Name: selector2._domainkey Type: CNAME Value: selector2-._domainkey..onmicrosoft.com.
The value for tenant name can be found when you look at your domain overview The value for the domain name is the domain that you setup here, replace the “.” for a “-”. For my domain worktogether.tech, this will be worktogether-tech
After adding the DNS records, you need to go to Exchange Online Admin page and enable DKIM. This page can be found under “Protection” 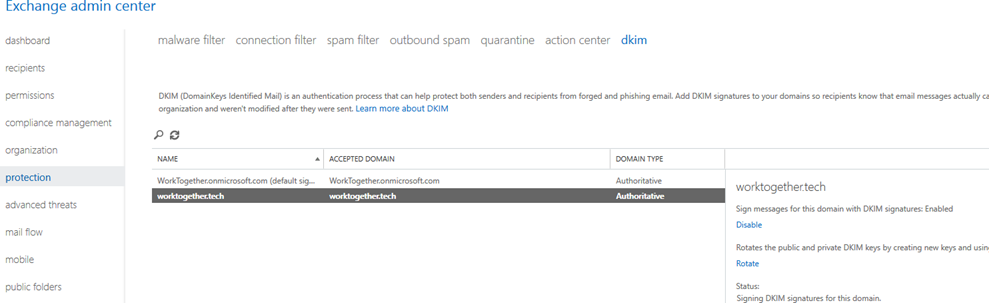 Select here the domain that you configured the DNS for and click ‘Enable’. This will enable DKIM for that domain, it is not show directly and can take a few moments.
Select here the domain that you configured the DNS for and click ‘Enable’. This will enable DKIM for that domain, it is not show directly and can take a few moments.
Safe attachments
This feature is available when you have Office 365 E5 or as an addon for other subscriptions. It allows Microsoft to scan every attachment that arrives from the outside world for malicious content. This is also available for content in SharePoint, OneDrive and Microsoft Teams. When you have the license it can be setup by creating a Safe Attachments policy in Exchange Online admin, here you can also enable it for SharePoint, OneDrive and Microsoft Teams 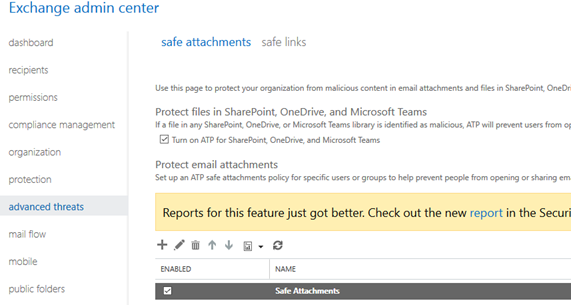
A policy is scoped to a user, group of users or domain. When using a group, this group must be a mail enabled security group
Safe links
For this feature, the same license is needed as Safe attachments. It has two separate policies that you can create. A policy that applies to the whole company and a policy for specific recipients. The company wide policy allows you to block certain URL’s set settings outside the email content. This means enabling it for Office 365 ProPlus and Office for iOS and Android The recipient policy is for all the settings applied to email and is scoped to a user, group of users or domain just like Safe attachments. A new feature that is rolling out during the writing of the article is that you can apply safe links also for emails that are send within the company. This is useful when a mailbox is hacked, and malicious links are send from that mailbox.
Message encryption
This feature allows you to encrypt email based on an automatic rule or let users encrypt certain email their self. It has a dependency on Azure information protection. It is available for users that have an E3 subscription or above The best way to enable this is to use PowerShell and you need the module “aadrm” and a connection to Exchange Online, follow this manual from Microsoft to configure or look at the blog from Albert Hoitingh.
For automatic message encryption, you can create mail flow rules in the Exchange admin center. 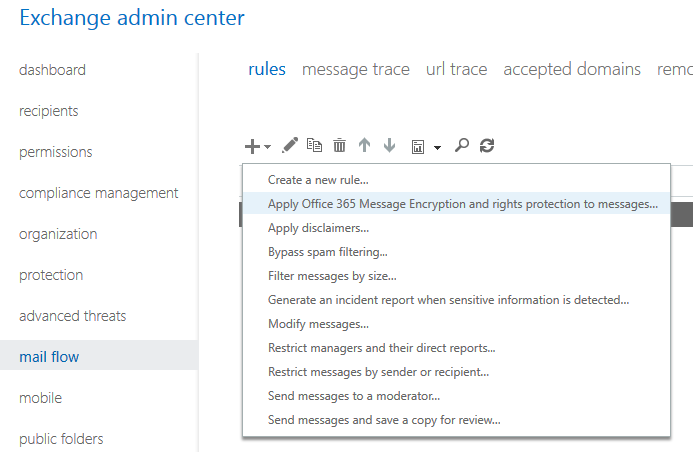
Do not forget to include the rule “The recipient is located” and set the value to “Outside the organization”. See this other post from Albert Hoitingh on more and detailed scenario’s.
Security and Compliance center
Most of these settings are also in the Security and Compliance Center. Here you can also see the latest trends in email attacks and use the attack simulator to identify vulnerable users
Resources
https://technet.microsoft.com/en-us/library/mt734386(v=exchg.150).aspx (Use DMARC to validate email in Office 365) https://technet.microsoft.com/en-us/library/mt695945(v=exchg.150).aspx (Use DKIM to validate outbound email sent from your custom domain in Office 365) https://support.office.com/en-us/article/Set-up-Office-365-ATP-safe-attachments-policies-078eb946-819a-4e13-8673-fe0c0ad3a775 (Set up Office 365 ATP safe attachments policies) https://support.office.com/en-us/article/set-up-new-office-365-message-encryption-capabilities-built-on-top-of-azure-information-protection-7ff0c040-b25c-4378-9904-b1b50210d00e (Set up new Office 365 Message Encryption capabilities built on top of Azure Information Protection) https://support.office.com/en-us/article/Office-365-Message-Encryption-FAQ-0432dce9-d9b6-4e73-8a13-4a932eb0081e (Office 365 Message Encryption FAQ)